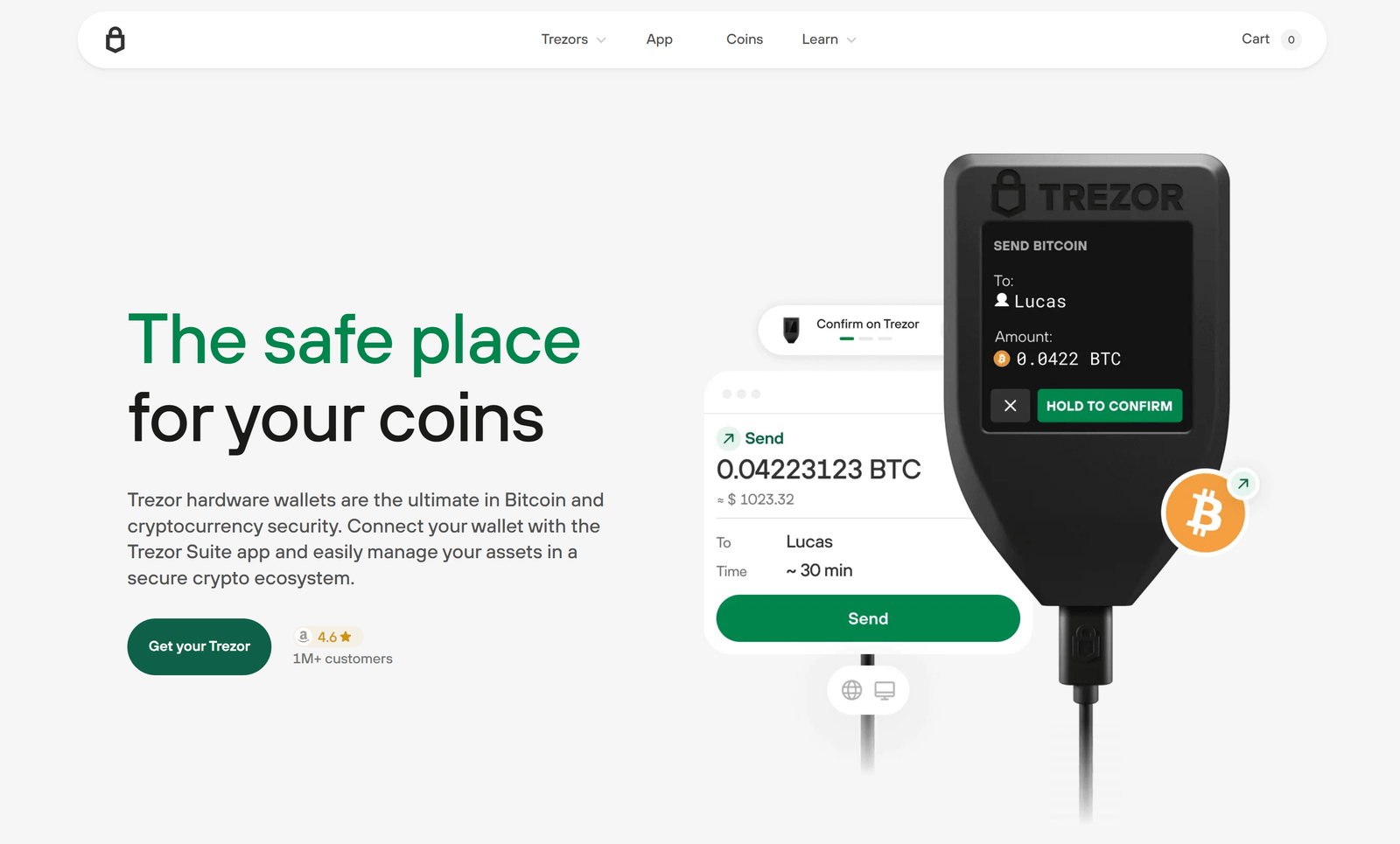
What Is Trezor Bridge?
Trezor Bridge is a lightweight communication software developed by Trezor.io. It connects your hardware wallet directly to your computer, enabling Trezor Suite to recognize your device securely.
- Provides encrypted and private communication channels.
- Works across Windows, macOS, and Linux.
- Eliminates the need for browser extensions.
- Completely open-source and reviewed by global security experts.
Note: Trezor Bridge runs quietly in the background and automatically detects your device for seamless usage.
How to Download & Install
- Visit the official download page: trezor.io/bridge.
- Choose your operating system and download the installer.
- Follow the installation instructions on-screen.
- Restart your browser or system once complete.
- Connect your Trezor device and open Trezor Suite to confirm connection.
Security Reminder: Only download Trezor Bridge from official Trezor sources. Avoid third-party sites to protect against malware and phishing attempts.
Why Choose Trezor Bridge?
- Secure Communication: Directly links Trezor Suite and your wallet via encrypted channels.
- Offline Key Safety: Your recovery seed and private keys never leave the device.
- Reliable Performance: Lightweight software with automatic detection.
- Cross-Platform: Fully compatible with all major operating systems.
- Transparency: 100% open-source and verifiable by the public.
Frequently Asked Questions
- 1. What is the main purpose of Trezor Bridge?
- It ensures a secure connection between your computer and Trezor wallet for safe crypto management through Trezor Suite.
- 2. Is it necessary to use Trezor Bridge?
- Yes, it’s required for browsers or systems that don’t natively support direct USB connections to hardware wallets.
- 3. Is Trezor Bridge free to use?
- Yes. It’s an official, open-source utility available at no cost.
- 4. How can I ensure I’m downloading safely?
- Always download directly from the official Trezor website.
- 5. Do I need to keep it updated?
- Occasional updates improve compatibility and enhance connection stability — always keep your software current.
 Download Trezor Bridge
Download Trezor Bridge